Taking Measures to Prevent Security Threats
Appropriate security measures are required to reduce the risk of information leaks and use by unauthorized persons.
The personal information stored in the Address Book and highly confidential files handled by the machine are important information assets. They should be protected from being stolen or abused.
To ensure secure use of the machine, specify the settings of the machine properly according to the specified environments, user level, administrator load, and the company's information security policy.
The security measures and their settings are described below. Take appropriate measures according to the operation environment of the machine.
 : Basic security measures
: Basic security measures
 : Strong security measures taken by the functions of the machine
: Strong security measures taken by the functions of the machine
 : Stronger security measures using the options of this machine or external security functions
: Stronger security measures using the options of this machine or external security functions
Defining the administrator of the machine
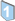 Select an administrator who performs the maintenance and management of the machine. The administrator performs the important security settings.
Select an administrator who performs the maintenance and management of the machine. The administrator performs the important security settings.
Preventing unauthorized access by managing the users who can use the machine or the connected network
 /
/  /
/  The administrator restricts the users who can use the machine to prevent the unauthorized access by unauthorized persons.
The administrator restricts the users who can use the machine to prevent the unauthorized access by unauthorized persons.
Verifying Users to Operate the Machine (User Authentication)
 Prevent a brute-force attack on the password or unauthorized operation of the machine caused by user inattentiveness.
Prevent a brute-force attack on the password or unauthorized operation of the machine caused by user inattentiveness.
When login is continuously fails due to an incorrect Login Password, login will be blocked.
If the machine is not used for a specified period after logging in, the user is forcibly logged out.
 Restrict the range of the IP addresses that are allowed to access the machine to block access to the machine from unauthorized computers. Also, specify the unused protocols to reduce the risk of intrusion.
Restrict the range of the IP addresses that are allowed to access the machine to block access to the machine from unauthorized computers. Also, specify the unused protocols to reduce the risk of intrusion.
 /
/  Prevent the leak or falsification of information by encrypting communication.
Prevent the leak or falsification of information by encrypting communication.
Preventing the leak of information by handling files

 Restrict browsing of files stored in the machine or the Address Book to protect the leak of information by unauthorized persons.
Restrict browsing of files stored in the machine or the Address Book to protect the leak of information by unauthorized persons.
Preventing Information Leaks by Sending Data to a Wrong Destination
 Restrict the manual input of the destination to avoid wrong transmission by careless mistake.
Restrict the manual input of the destination to avoid wrong transmission by careless mistake.
Preventing Information Leaks by Sending Data to a Wrong Destination
 Restrict the connection of external media to avoid the data being removed.
Restrict the connection of external media to avoid the data being removed.
Preventing Information Leaks from the Media Slot
 /
/  Prevent unauthorized copying or printed paper stolen by embedding a pattern on the printed surface or restricting normal printing.
Prevent unauthorized copying or printed paper stolen by embedding a pattern on the printed surface or restricting normal printing.
Preventing Data Leaks from Printed Sheets
 Prevent the leak of information when the machine is stolen or disposed by encrypting data.
Prevent the leak of information when the machine is stolen or disposed by encrypting data.
Encrypting Data to Prevent Data Leaks Caused by a Stolen or Disposed Machine
 Restrict the operation in Service Mode used for maintenance and repair by a customer engineer to prevent the leak of information.
Restrict the operation in Service Mode used for maintenance and repair by a customer engineer to prevent the leak of information.
Restricting Operations of the Customer Engineer without the Supervision of the Machine Administrator

To prevent this machine from being stolen or willfully damaged, install it in a secure location.
If the security settings are not configured, the data in the machine may be vulnerable to attack.
Select a person who can responsibly use the machine as the machine administrator, and use the machine appropriately.
Before setting this machine's security features, the administrators must read the descriptions on security completely and thoroughly. Pay particular attention to the section entitled Registering Administrators Before Using the Machine.
Administrators must inform users regarding proper usage of the security functions.
If this machine is connected to a network, its environment must be protected by a firewall or similar security measure.
For protection of data during communication, apply the machine's communication security functions and connect it to devices that support security functions such as encrypted communication.
Administrators should regularly examine the machine's logs to check for irregular and unusual events.
Checking Firmware Validity
When the machine starts up, this function is used to check that the firmware is valid.
If an error occurs while a verification process is performed, a verification error is displayed on the control panel.
Note that this can also be checked on Web Image Monitor after the machine starts. If an error occurs in a verification process of Web Image Monitor, Web Image Monitor cannot be used. If this is the case, check the control panel.
