Access Control
The administrator can limit devices or protocols that can be connected to the machine to avoid unintended access.
Also, the administrator can configure the port status.
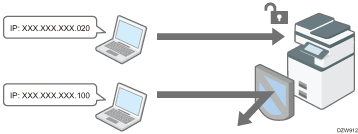
Limiting the IP addresses from which devices can access the machine (Access Control)
For example, when specifying the range of IP address from "192.168.15.1" to "192.168.15.99", the machine cannot be accessed from IP addresses in the range from 192.168.15.100 to 255.
Disabling unused protocols
The protocol setting can be changed on the control panel, in Web Image Monitor, or by using other setting methods. The protocols that can be configured vary depending on the method. Confirm the protocol to configure in Protocol Setting Method List and follow the instruction.
Limiting the IP Addresses from which Devices Can Access the Machine
Specify the range of the IP address that can access the machine by using Web Image Monitor.
![]()
You can limit access from the following protocols.
LPR, RCP/RSH, FTP, Bonjour, SMB, WSD (Device), WSD (Printer), IPP, DIPRINT, snmp, telnet
The machine also limits access from Web Image Monitor.
![]() Log in to the machine as the administrator from Web Image Monitor.
Log in to the machine as the administrator from Web Image Monitor.
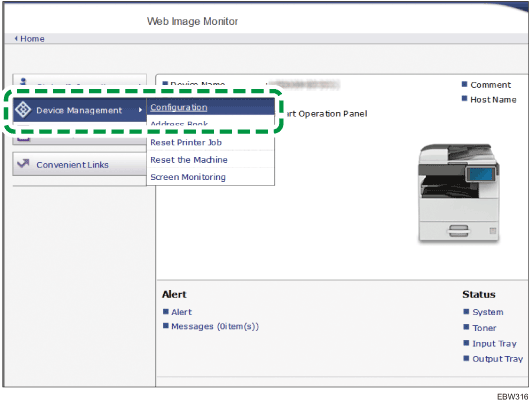
![]() Click [Configuration] from the [Device Management] menu.
Click [Configuration] from the [Device Management] menu.
![]() Click [Access Control] in "Security".
Click [Access Control] in "Security".
![]() To specify an IPv4 address, enter a range that has access to the machine in "Access Control Range".
To specify an IPv4 address, enter a range that has access to the machine in "Access Control Range".
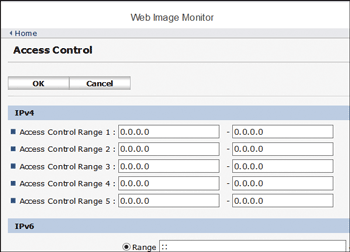
To specify an IPv6 address, select "Range" or "Mask" in "Access Control Range", and then enter a range that has access to the machine.
![]() Click [OK].
Click [OK].
![]() After completing the configuration, click [OK] and exit the Web browser.
After completing the configuration, click [OK] and exit the Web browser.
Protocol Setting Method List
You can view the protocol setting methods in the following list:
1: Control Panel 2: Web Image Monitor 3: telnet 4: Device Manager NX 5: Remote Communication Gate S
Protocol/Port | Setting method | Function that cannot be used when Protocol/Port is disabled |
|---|---|---|
IPv4 - | 1, 2, 3 | All applications that operate over IPv4 (IPv4 cannot be disabled from Web Image Monitor when using IPv4 transmission.) |
IPv6 - | 1, 2, 3 | All applications that operate over IPv6 |
FTP TCP:21 | 2, 3, 4, 5 | Transmissions that require FTP (You can restrict only the personal information from being displayed by settings on the control panel.) |
telnet TCP:23 | 2, 4 | Transmissions that require telnet |
HTTP TCP:80 | 2, 3 | Transmissions that require HTTP Print using IPP on port 80 |
HTTPS TCP:443 | 2, 3 | Transmissions that require HTTPS (You can make settings to require SSL transmission only and to reject non-SSL transmission using the control panel or Web Image Monitor.) RICOH @Remote |
SNMPv1-v2 UDP:161 | 2, 3, 4, 5 | Transmissions that require SNMPv1/v2 (Using the control panel, Web Image Monitor, or telnet, you can specify SNMPv1/v2 to prohibit configuration and make it read-only.) |
SNMPv3 UDP:161 | 2, 3, 4, 5 | Transmissions that require SNMPv3 (You can make settings to require SNMPv3 encrypted transmission only and to reject non-SNMPv3 encrypted transmission using the control panel, Web Image Monitor, or telnet.) |
RSH/RCP TCP:514 | 2, 3, 4, 5 | Transmissions that require RSH Network TWAIN (You can prohibit only personal information from being displayed by the settings on the control panel.) |
LPR TCP:515 | 2, 3, 4, 5 | Transmissions that require LPR (You can restrict only personal information from being displayed by the settings on the control panel.) |
IPP TCP:631 | 2, 3, 4, 5 | Transmissions that require LPR |
Bonjour UDP:5353 | 2, 3 | Transmissions that require Bonjour |
@Remote TCP:7443 TCP:7444 | 1, 3 | RICOH @Remote |
DIPRINT TCP:9100 | 2, 3, 4, 5 | Transmissions that require DIPRINT |
RFU TCP:10021 | 1, 3 | Remote updating of firmware |
WSD (Device) TCP:53000 (variable) | 2, 3 | Transmissions that require WSD (Device)
|
WSD (Printer) TCP:53001 (variable) | 2, 3 | Transmissions that require WSD (Printer) |
LLMNR UDP:5355 | 2, 3 | Name resolution requests using LLMNR |
![]()
For details about the setting procedure on the control panel or from Web Image Monitor, see the following instructions:
For details about the telnet command, see "Device Monitoring (TELNET)" on our website.
For details about the settings in Device Manager NX or Remote Communication Gate S, see the user's manual of each tool.
Disabling Unused Protocols from the Control Panel
Configure protocols on [System Settings]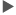 [Interface Settings].
[Interface Settings].
![]() Log in to the machine as the administrator on the control panel.
Log in to the machine as the administrator on the control panel.
![]() On the Home screen, press [Settings].
On the Home screen, press [Settings].
![]() Press [Machine Features Settings] on the Settings screen.
Press [Machine Features Settings] on the Settings screen.
![]() Press [System Settings]
Press [System Settings] [Interface Settings]
[Interface Settings] [Network]
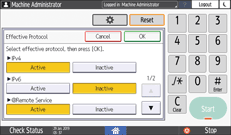
[Network] [Effective Protocol] to display the setting screen of each protocol.
[Effective Protocol] to display the setting screen of each protocol.
![]() Disable unused protocols.
Disable unused protocols.
![]() Press [OK].
Press [OK].
![]() After completing the configuration, press Home (
After completing the configuration, press Home ( ).
).
Disabling Unused Protocols from Web Image Monitor
Configure protocols on [Settings] the "Security" category.
the "Security" category.
![]() Log in to the machine as the administrator from Web Image Monitor.
Log in to the machine as the administrator from Web Image Monitor.
![]() Click [Configuration] from the [Device Management] menu.
Click [Configuration] from the [Device Management] menu.

![]() Click [Network Security] in "Security".
Click [Network Security] in "Security".
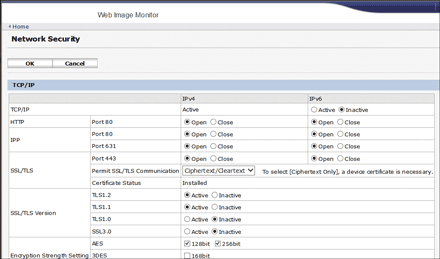
![]() Specify protocols to disable or port numbers to close.
Specify protocols to disable or port numbers to close.
![]() Click [OK].
Click [OK].
![]() After completing the configuration, click [OK] and exit the Web browser.
After completing the configuration, click [OK] and exit the Web browser.
