Restricting Usage of the Destination List
The use of the destination list can be restricted separately under the fax and scanner functions.
Restrict Use of Destinations (Fax), Restrict Use of Destinations (Scanner)
You can prohibit the sending of faxes and scanned documents to addresses other than those registered in the Address Book. By enabling this, you can prohibit users from manually entering the parties’ fax number, e-mail address or folder destinations.
Restrict Adding of User Destinations (Fax), Restrict Adding of User Destinations (Scanner)
By using [Prg. Dest.], you can prohibit the addresses manually entered for sending faxes or scanned documents from being registered to the Address Book. Also, with this setting, only the user administrator can register new users in the Address Book and change the passwords and other information of existing registered users. In addition, even if you set these functions to [On], the user registered as a destination can change their password. Only the user administrator can change items other than the password.
![]() Log in as the user administrator from the control panel.
Log in as the user administrator from the control panel.
For details on how to log in, see Administrator Login Method.
![]() Press [System Settings].
Press [System Settings].
![]() Press [Administrator Tools].
Press [Administrator Tools].
![]() Press [
Press [![]() Next] twice.
Next] twice.
![]() Press [Extended Security].
Press [Extended Security].
![]() Press [
Press [![]() Next].
Next].
![]() Set "Restrict Use of Destinations" or "Restrict Adding of User Destinations" to [On].
Set "Restrict Use of Destinations" or "Restrict Adding of User Destinations" to [On].
Specify these settings for both fax and scanner functions.
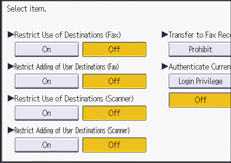
If you set "Restrict Use of Destinations (Fax)" to [On], "Restrict Adding of User Destinations (Fax)" will not appear. Similarly, if you set "Restrict Use of Destinations (Scanner)" to [On], "Restrict Adding of User Destinations (Scanner)" will not appear.
![]() Press [OK].
Press [OK].
![]() Log out.
Log out.
For details about logging out, see Administrator Logout Method.
![]()
The extended security functions can also be specified using a web browser from networked computers. (We use Web Image Monitor installed on this machine.) For details, see Web Image Monitor Help.
