Confirming Log Files
You can download the logs of the machine as CSV files using Web Image Monitor. It depends on the log type (Job Log, Access Log, or Eco-friendly Logs) how to read the files.
For the log type, see the following section:
Log Data Format
Output Format of Files
Item | Description |
|---|---|
Character Set | UTF-8 JIS |
Output Format | CSV (Comma-Separated Values) format |
File Name of Job Log+Access Log | "Machine Name_log.csv" |
File Name of Job Log | "Machine Name_joblog.csv" |
File Name of Access Log | "Machine Name_accesslog.csv" |
File Name of Eco-friendly Log | "Machine Name_ecolog.csv" |
Order of Logs
Logs are output in ascending order of Log ID ("Log ID").
File Configuration
Title of each data is output on the first line of the file (header line).
Difference in Log Data Format
Job Log
Common items, sources, and targets that have common log ID are output in three or more lines in configuration as shown below.
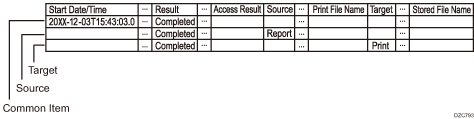
Name
Description
Common Item
Common items of job log and access log are output in one line.
Source
Outputs the "Result", "Status", and job-log input information of common items. When there are multiple sources, multiple lines are output.
Target
Outputs the "Result", "Status", and job-log output information of common items. When there are multiple targets, multiple lines are output.
Access Log
Common items and access log are output in one line.
Eco-friendly Logs
Eco-friendly Logs information is output in one line.
Common Items (Job Log and Access Log)
Titles shown below are the text displayed on the header line of the CSV file.
Start Date/Time
Stores the Start Date/Time of the operation and event.
End Date/Time
Stores the End Date/Time of the operation and event.
Log Type
Result
Stores the results of the operation or event.
"Stored File Deletion" of the access log is stored as log only when the event succeeds.
Item | Description |
|---|---|
Failed | Operation or event failed |
Succeeded | Operation or event completed |
<blank> | Operation or event processing |
Operation Method
Stores the operations.
Item | Description |
|---|---|
Control Panel | Control panel |
Driver | Driver |
Utility | Utility |
Web | Web |
Status
Stores the status of operations or events.
Item | Description |
|---|---|
Authentication Method Mismatch | Authentication mode mismatch |
Authentication Settings Mismatch | Specification in the Address Book mismatch |
Common Key Not Exist | Common key not exist |
Communication Failure | Communication failed |
Communication Result Unknown | Communication results unknown |
Completed | Operation Completed |
Connection Error | Connection error |
Connection Failed with Remote Machine | Connection with remote machine failed |
Decoding Failed | Decoding failed |
Encryption Failed | Encryption failed |
Error | Error |
Failed | Operation failed |
Failure in some or all parts | Failure in some or all parts |
File Limit Exceeded | Capture error because of the file limit is exceeded |
Functional Problem | Capture error because of device trouble |
Importing/Exporting by Other User | Importing/Exporting by other users progressing |
Invalid Password | Path code error |
Lost File | Capture error because of file lost |
Maximum Limit of Registered Number | Maximum limit of registered number of central management |
Memory Storage Device Error | Memory storage device error |
Memory Storage Device Full | Full capacity of the memory storage device |
Other Failures | Other failures |
Password Mismatch | Password mismatch |
Power Failure | Capture error because of power failure |
Processing | Processing |
Specified Client Error | Client unspecified error |
Specified File: Access Error | Access error to the specified file |
Specified File: Format Error | Format error of the specified file |
Specified File: Incompatible | Incompatible with the specified file |
Specified File: No Privileges | No privileges to the specified file |
Specified File: Not Exist | No specified file exist |
Specified Server Error | Server unspecified error |
Succeeded | Operation succeeded |
Suspended | Suspended |
Transfer Canceled | Error by canceling capture transfer |
User Cancel | Canceled by the user |
User Locked Out | The user locked out |
User Not Programmed | User not programmed |
Write Error to Remote Machine | Writing error to remote machine |
Cancelled: Details
Stores the status of the failed operations or events.
Item | Description |
|---|---|
Authentication Failed (Access Restricted) | Authentication of the machine failed. |
Authentication Failed with Destination | Authentication of the destination failed. |
Cancelled by User | Canceled by users |
Connection Failed with Destination | Specified server or folder is not found. |
Data Transfer Interrupted | Stored in the following cases:
|
Exceed Max. Stored File (File Storage) | Exceeds the maximum number of files storable in Document Server |
Exceed Max. Stored Page (File Storage) | Exceeds the maximum number of pages storable in Document Server |
Exceed Max. Stored Page (Image Area) | Exceeds the maximum number of pages that can be captured |
Exceeded Max. Email Size | Exceeds the maximum e-mail size |
Exceeded Max. File Size | Exceeds the maximum size of a file |
Exceeded Print Volume Use Limitation | Exceeds the number of Print Volume Use limitation of the login user. |
Exceeded Print Volume Use Limitation: Communication Error | For central management of Print Volume Use, communication error is generated with the central management server. |
Exceeded Print Volume Use Limitation: No Remaining Print Volume | For central management of Print Volume Use, the machine failed to obtain the point because the remaining point is assigned to another client device. |
External Charge Unit Disconnected | External charge unit disconnected during operation |
Folder is Locked | The folder is locked. |
Hard Disk Full (File Storage Memory) | Exceeds the maximum capacity of the hard disk storable in Document Server |
Hard Disk Full (Image Area) | Exceeds the capacity of the hard disk that can be captured |
Input Failure | Input operation failed |
Insufficient No. of Original for Overlay | Insufficient number of pages of the original for overlay |
Invalid Device Certificate | The device has no Device Certificate, Term of Validity is expired, or e-mail address of the Administrator does not match the e-mail address of the Certificate. |
Invalid Device/Destination's Certificate | Both Destination's Certificate and Device Certificate are not authorized. |
Invalid Expiration Date: Destination's Certificate | Validity Period of the destination is expired. |
Line Busy | The destination is busy. |
Memory Full | The memory for processing data is full. |
No Privilege | No privilege to use files or functions |
No Response | No response on the destination |
Not Entered Document Password | Password for the file is not entered. |
Not Facsimile Destination | The destination is not a facsimile. |
Other Error | Errors detected before executing the job or other errors |
Output Failure | Output operation failed |
Over Job Limit | Exceeds the number of jobs that can be received |
Password for Folder Specified to Store is Incorrect | Password for the specified folder to store data is incorrect. |
Power Failure | Power failure |
Print Cancelled (Error) | The system cancels the job. |
Print Data Error | PDL or port that is not equipped with the machine is used. |
Reception Error | Fax reception failed |
Scanner Error | Scanning error on ADF |
Specified Folder to Store does not Exist | A specified folder to store data does not exist. |
Specifying Destination Error | An unauthorized destination is specified or the specified digit for the destination exceeds 41. |
Specifying Line Error | Specified line is incorrect. |
Timeout | Timeout |
Transmission Failed (Data Deleted) | The transmitted file or the undelivered file whose storage period is expired is deleted. |
Transmission Failed with Memory Full | Capacity of the destination memory is full. |
Unavailable Size to Store | The specified paper size (including custom size) is unavailable to store. |
User Entry ID
Stores the Entry ID.
This is a unique ID for the user requested the job log and access log of operations. It is output as a hexadecimal number.
Item | Description |
|---|---|
0x00000000 | System operation or unauthorized user's operation |
0x00000001 to 0xfffffeff | User and User Code |
0xffffff80 | System operation |
0xffffff81 | System operation or unauthorized user's operation |
0xffffff86 | Supervisor |
0xffffff87 | Administrator 1 |
0xffffff88 | Administrator 2 |
0xffffff89 | Administrator 3 |
0xffffff8a | Administrator 4 |
0xffffff8b | For counting |
User Code/User Name
For the user's operation, User Code or Login User Name is stored.
For an Administrator, Administrator's Login User Name is stored.
Log ID
The log stores an ID. It is a unique ID for the log and is output as a hexadecimal number.
Job Log Input Information
Titles shown below are the text displayed on the header line of the CSV file.
Source
Stores the input information of the job log.
Item | Description |
|---|---|
Printer | Print indication on the printer driver |
Received File | Fax Reception |
Report | Report printing |
Scan File | Scanning originals |
Stored File | Storing files |
Start Date/Time
When the input information is "Scan File", "Printer" or "Received File", Start Date/Time of the input information is stored.
End Date/Time
When the input information is "Scan File", "Printer" or "Received File", End Date / Time of the input information is stored.
Stored File
When the input information is "Stored File", ID is stored.
It is a unique ID for the file and is output as a decimal number.
Stored File Name
When the input information is "Stored File", File Name is stored.
Folder Number
Memorized Folder Number is stored.
Folder Name
Memorized Folder Name is stored.
Print File Name
When the input information is "Printer", File Name of the print file is stored.
Job Log Output Information
Titles shown below are the text displayed on the header line of the CSV file.
Target
Stores the output information of the job log.
Item | Description |
|---|---|
Send | Send |
Store | Store |
Start Date/Time
Sends the Start Date / Time to print, store, and send files.
End Date/Time
Sends the End Date / Time to print, store, and send files.
Destination Name
When the output information is "Send", Name of the destination is stored.
Destination Address
When the output information is "Send", IP Address, Path, or Email Address of the destination are stored.
Stored File ID
When the output information is "Store", ID is added.
It is a unique ID for the file and is output as a decimal number.
For the Fax function, "Stored File ID" is not stored in log.
Stored File Name
When the output information is "Store", File Name of the stored file is stored.
For the Fax function, "Stored File Name" is not stored in log.
Folder Number
Memorized Folder Number is stored.
Folder Name
Memorized Folder Name is stored.
Access Log
Titles shown below are the text displayed on the header line of the CSV file.
Access Log Type
Stores the type of the access log.
Item | Description |
|---|---|
Address Book | Address Book |
Authentication | User Authentication |
Device Settings | Changes the settings of the Settings |
Firmware | Confirming the firmware validity |
Network Attack Detection/Encrypted Communication | Network Attack or Encrypted Communication |
Stored File | File |
System | System |
Authentication Server Name
Stores the sever name that tried the last authentication.
No. of Authentication Server Switches
Stores how many times the server was switched when the Authentication server was down.
You can identify whether to detect the server down.
The number of switching the server is 0 to 4 times.
When 0, the server is not down.
Logout Mode
Stores the logout mode.
Item | Description |
|---|---|
by Auto Logout Timer | Auto logout of time |
by User's Operation | Logout operation by a user |
Login Method
Stores the route to receive Authentication Request
Item | Description |
|---|---|
Control Panel | Operation on the Control Panel |
Others | Requests from others |
via Network | Operation via the Network |
Login User Type
Stores the type of login user.
Item | Description |
|---|---|
Customer Engineer (Service Mode) | Customer engineer |
File Administrator | File Administrator |
Guest | Guest |
Machine Administrator | Machine Administrator |
Network Administrator | Network Administrator |
Others | Login by users other than described above. |
Supervisor | Supervisor |
User | Authentication user |
User Administrator | User Administrator |
Target User Entry ID
Stores the Entry ID to the target
It is a unique ID for the target user of the operation described below and is output as a hexadecimal number.
Lockout operation
Change password
Target User Code/User Name
Stores User Code or User Name of the target.
When the target is an Administrator, Login User Name of the Administrator is stored.
Address Book Registration No.
Stores the registration number of the user who operates the machine.
Address Book Operation Mode
Stores how the Address Book is changed.
Address Book Change Item
Stores which item in the Address Book is changed.
Address Book Change Request IP Address
Stores the IP address information (IPV4/IPV6) of the user who operates the Address Book.
Lockout/Release
Stores the lockout status.
Item | Description |
|---|---|
Lockout | The password is locked. |
Release | The lock is released. |
Lockout/Release Method
Stores how to release the lockout.
Item | Description |
|---|---|
Auto | Release lockout using the release timer |
Manual | Release lockout manually. |
Lockout Release Target Administrator
Stores the target Administrator when releasing lockout.
Counter to Clear
Stores which counter is cleared for each user.
Export Target
Stores the setting information of the target to export the device information.
Item | Description |
|---|---|
Browser Features | Browser settings |
Copier Features | Copy settings |
Fax Features | Fax settings |
Fax SP | Fax SP |
Printer Features | Printer settings |
Printer SP | Printer SP |
Program (Copier) | Program (Copy) |
Program (Document Server) | Program (Document Server) |
Program (Scanner) | Program (Scanner) |
Scanner Features | Scanner settings |
Scanner SP | Scanner SP |
System Settings | System settings |
System/Copier SP | System/Copier SP |
Web Image Monitor Setting | Web Image Monitor Settings |
Web Service Settings | Web service settings |
Target File Name
Stores the File Name of the target to import and export the device information.
Stored File ID
Stores the ID for the created or deleted file.
It is a unique ID for the create- or delete-request file and is output as a decimal number.
Stored File Name
Stores the File Name of the created or deleted file.
Delete File Type
Stores the type of the delete file.
Item | Description |
|---|---|
Auto Delete | Auto Delete |
Delete Editing File | Deletion during editing |
Delete Normal File | Normal file delete |
Others | Delete because of other reasons |
Folder Number
Stores Folder Number.
Folder Name
Stores Folder Name.
Creating/Deleting Folders
Stores how to operate the folder.
Item | Description |
|---|---|
Delete Folder | Delete a folder |
New Folder | Creates a new folder. |
File Location
Stores the target area for deleting all files.
Collect Job Logs
Stores whether to change the settings of Collect Job Logs.
Item | Description |
|---|---|
Active | Changes to Active. |
Inactive | Changes to Inactive. |
Not Changed | Not changed |
Collect Access Logs
Stores whether to change the settings of Collect Access Logs.
Item | Description |
|---|---|
Active | Changes to Active. |
Inactive | Changes to Inactive. |
Not Changed | Not changed |
Collect Eco-friendly Logs
Stores whether to change the settings of Collect Eco-friendly Logs.
Item | Description |
|---|---|
Active | Changes to Active. |
Inactive | Changes to Inactive. |
Not Changed | Not changed |
Transfer Logs
Stores whether to change the settings of transfer log function.
Item | Description |
|---|---|
Active | Changes to Active. |
Inactive | Changes to Inactive. |
Not Changed | Not changed |
Log Type
Stores the log type for the target to change the collect log status.
Item | Description |
|---|---|
Access Log | Access Log |
Collect Eco-friendly Logs | Eco-friendly Logs |
Job Log | Job Log |
Log Collect Level
Stores the log level settings.
Item | Description |
|---|---|
Level 1 | Level 1 |
Level 2 | Level 2 |
User Settings | User settings |
Encryption/Cleartext
Stores the status, encryption communication status or cleartext communication status.
Item | Description |
|---|---|
Cleartext Communication | Cleartext communication |
Encryption Communication | Encryption communication |
Machine Port No.
Stores the Port Number of the machine.
Protocol
Stores the target protocol.
When it is not specified, "Unknown" is stored.
IP Address
Stores the target IP address.
Port No.
Stores the Port Number of the target.
It is output as a decimal number.
MAC Address
Stores the target MAC Address.
Primary Communication Protocol
Stores the primary communication protocol name.
Secondary Communication Protocol
Stores the secondary communication protocol name.
Encryption Protocol
Stores the Encryption protocol name.
Communication Direction
Stores the communication direction.
Item | Description |
|---|---|
Communication Start Request Receiver (In) | Receiver of the communication start request (IN) |
Communication Start Request Sender (Out) | Sender of the communication start request (OUT) |
Communication Start Log ID
Stores the log ID when starting communication.
It is a unique ID for the log of starting communication and is output as a hexadecimal number.
Communication Start/End
Stores the identifier to identify the communication start and end.
Network Attack Status
Stores the status of attack detection.
Item | Description |
|---|---|
Max. Host Capacity Reached | The maximum host capacity is reached and the management is disabled. |
Recovered from Max. Host Capacity | Recovers from the host management disabled. |
Recovered from Violation | Detects the network attack recovery. |
Violation Detected | Detects the network attack. |
Network Attack Type
Stores the type of attack.
Item | Description |
|---|---|
Device Access Violation | Authentication DoS violation |
Password Entry Violation | Password violation |
Request Falsification Violation | Request falsification |
Network Attack Type Details
Stores the details about the type of attacks.
Item | Description |
|---|---|
Authentication Error | Authentication error |
Encryption Error | Encryption error |
Network Attack Route
Stores the attack route.
Item | Description |
|---|---|
Attack from Control Panel | Attacked from the Control Panel. |
Attack from Other than Control Panel | Attacked from other than the Control Panel. |
Login User Name used for Network Attack
Stores the login user name used for network attack.
Add/Update/Delete Firmware
Stores the firmware change system.
Item | Description |
|---|---|
Added with SD Card | Added with the SD card. |
Deleted with SD Card | Deleted with the SD card. |
Moved to Another SD Card | Moved to another SD card. |
Updated for Other Reasons | Update for other reasons. |
Updated via Remote | Updated via remote. |
Updated with SD Card | Update with the SD card. |
Module Name
Stores the Module Name of the firmware.
Parts Number
Stores the part number of the firmware.
Version
Stores the firmware version.
Machine Data Encryption Key Operation
Stores the encryption key operation mode.
Item | Description |
|---|---|
Back Up Machine Data Encryption Key | The Encryption Key is backed up. |
Clear NVRAM | NVRAM is cleared. |
Finish Updating Machine Data Encryption Key | Updating the Encryption Key ends. |
Restore Machine Data Encryption Key | The Encryption Key is restored. |
Start Updating Machine Data Encryption Key | Updating the Encryption Key starts. |
Machine Data Encryption Key Operation
Stores the type of the encryption key.
Item | Description |
|---|---|
Device Certificate | Device certificate |
Encryption Key for Hard Disk | HDD Encryption Key |
Encryption Key for NVRAM | NVRAM Encryption Key |
Validity Error File Name
Stores the File Name when the validity verification error is detected.
Configuration Category
Stores the category whose settings are changed.
Item | Description |
|---|---|
Auto Logout Timer | Auto logout time settings |
Compulsory Security Stamp | Compulsory security stamp |
Device Certificate | Device certificate |
Extended Security | Extended Security |
Firmware Update Start | Update Firmware |
IPsec | IPsec |
Prohibit printing stored files from Web Image Monitor | Prohibits the output of the stored files with Web Image Monitor. |
S/MIME | S/MIME |
User Lockout Policy | User lockout |
WIM Auto Logout Timer | Auto logout time settings for Web Image Monitor |
Configuration Name / Configuration Value
Stores the attributes of the categories.
Stores the value of attributes.
Item | Description |
|---|---|
Auto Logout Timer | On or Off of Auto Logout Time settings |
Auto Logout Timer (seconds) | Time to activate Auto Logout |
Certificate No. | Certificate number of the operation target |
Certificate No.: Digital Signature PDF | Certificate number used with the application When you do not use Certificate, "Do not Use" is stored. |
Certificate No.: Digital Signature PDF/A | Certificate number used with the application When you do not use Certificate, "Do not Use" is stored. |
Certificate No.: IEEE 802.1X (WPA/WPA2) | Certificate number used with the application When you do not use Certificate, "Do not Use" is stored. |
Certificate No.: IPsec | Certificate number used with the application When you do not use Certificate, "Do not Use" is stored. |
Certificate No.: S/MIME | Certificate number used with the application When you do not use Certificate, "Do not Use" is stored. |
Change Firmware Structure | Change of [Change Firmware Structure] "Prohibit" or "Do not Prohibit" is stored. |
Compulsory Security Stamp | On or Off of Compulsory Security Stamp: |
Document Server (Utility): Stored File Transferring | Signature for transferring stored files by Document Server (Utility) |
Encryption Key Auto Exchange: Setting1-4, Default Setting Authentication Method Mismatch | Authentication Method of Auto Key Replacement System Stores "PSK" or "Certificate". |
Encryption Key Auto Exchange: Setting1-4, Default Setting: Security Level | Security Level When you select "Authentication Only", "Authentication Only" is stored. When you select "Authentication and Low Level Encryption", "Authentication and Low Level Encryption" is stored. When you select "Authentication and High Level Encryption", "Authentication and High Level Encryption" is stored. When you select "User Settings", "User Settings" is stored. |
Encryption Key Auto Exchange: Setting1-4: Remote Address | Remote Address |
Fax: Email Sending | Signature for e-mail sending by Fax |
Fax: Notification Email Sending | Signature for message mail sending by Fax |
Fax: Transferring | Signature for transferring by Fax |
Firmware Update Start | Start of firmware update |
IPsec | Active or Inactive of IPsec |
Lock Out User for | Time to release lockout |
Lockout | Active or Inactive of lockout |
Lockout Release Timer | Active or Inactive of Lockout Release Timer |
Number of Attempts before Lockout | Allowable number of attempts to enter login password before lockout (time(s)) |
Operation Mode | Operation mode |
Prohibit printing stored files from Web Image Monitor | Change of [Prohibit printing stored files from Web Image Monitor]. "Prohibit" or "Do not Prohibit" is stored. |
Scanner: Email Sending | Signature for e-mail sending by Scanner |
Update Firmware | Change of [Firmware Update] "Prohibit" or "Do not Prohibit" is stored. |
WIM Auto Logout Timer (minutes) | Auto Logout Time (minutes) of Web Image Monitor |
Destination Server Name
When log type is "Enhanced Print Volume Use Limitation: Tracking Permission Result", stores the server name of the destination to which send of the tracking information is failed.
When the log type is import or export of the preference information, stores the server name of import request or export request.
HDD Format Partition
Stores the reason for reset of the hard disk.
Item | Description |
|---|---|
HDD Exchange | Detects the HDD change. |
Problem with Disk Label | Cannot read disk label. |
Problem with File System | File system error |
Problem with HDD Encryption Key | HDD Encryption Key error |
Access Result
Stores the results of operation that generates log.
Item | Description |
|---|---|
Completed | Operation Completed |
Failed | Operation failed |
Eco-friendly Logs
Titles shown below are the text displayed on the header line of the CSV file.
Start Date/Time
Stores the Start Date/Time of the event.
End Date/Time
Stores the End Date/Time of the event.
Log Type
Stores the type of the Eco-friendly log.
Item | Description |
|---|---|
Job Related Information | Log for job related information |
Main Power Off | Log when the main power is turned off. |
Main Power On | Log when the main power is turned on. |
Paper Usage | Log for paper usage |
Power Consumption | Log for power consumption |
Power Status Transition Result | Log for power status transition result |
Log Result
Indicates whether the even ends.
Item | Description |
|---|---|
Completed | Operation Completed |
Failed | Operation failed |
Result
Stores the results of events.
Item | Description |
|---|---|
Failed | Event failed |
Succeeded | Event succeeded |
Log ID
Stores an ID specified the log. ID is a hexadecimal number.
Power Mode
Stores the power status of the machine (after transition) as a log.
Item | Description |
|---|---|
Controller Off | Status of the controller Off |
Engine Off | Status of the engine Off |
Fuser Unit Off | Status of fuser unit Off |
HDD On | Status of the hard disk startup |
Low Power | Lower poser status |
Low Power Print | Lower power print status |
Silent | Silent mode |
Silent Print | Silent print status |
Standby | Standby status |
STR | Status of STR (Suspend To RAM) |
Log Type
Stores the type of the job log.
Job Interval (seconds)
Stores the elapsed time from the start of the previous job to that of the current job.
Job Duration (seconds)
Stores the elapsed time from the start of the previous job to that of the current job.
Paper Usage (Large Size)
Stores the usage of 1-sided large size paper per hour.
Large size paper means A3 or 11 × 17 inches or larger.
Paper Usage (Small Size)
Stores the usage of 1-sided small size paper per hour.
Small size paper means smaller than A3 or 11 × 17 inches.
Paper Usage (2 Sided: Large Size)
Stores the usage of 2-sided large size paper per hour
Large size paper means A3 or 11 × 17 inches or larger.
Paper Usage (2 Sided: Small Size)
Stores the usage of 2-sided small size paper per hour.
Small size paper means smaller than A3 or 11 × 17 inches.
Detected Power
Stores the power status of the machine, whose power consumption is measured, as log.
Item | Description |
|---|---|
Controller Standby | Controller standby status |
Engine Low | Engine low power status |
Engine Night | Engine silent mode |
Engine Standby | Engine standby status |
Engine Total | Overall status of the machine |
Fuser Unit Off | Fuser Unit standby status |
Main Power Off | The main power is turned Off. |
Printing | Printer is processing. |
Scanning | Scanner is processing. |
Scanning/Printing | Printer and Scanner are processing. |
STR | Status of STR (Suspend To RAM) |
Power Consumption(Wh)
Stores the power consumption for each power status.
