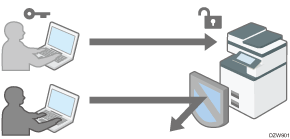
Taking Measures to Prevent Unauthorized Access
Specify the machine to prevent access by anyone from any location so as to protect the information asset. You can prevent unauthorized access by restricting the users who can use the machine and encrypting or restricting the network.
Specifying user authentication
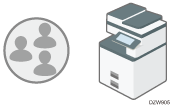
The administrator registers the users on the machine and only the registered users can use the machine.
Verifying Users to Operate the Machine (User Authentication)
Specifying the authentication policy
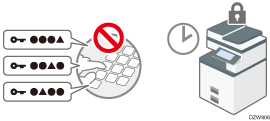
Specify how many times entering an incorrect password is allowed and the auto-logout time when you do not operate the machine for a specified period of time to protect the machine from unauthorized use.
Restricting the network connection
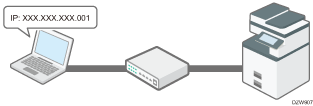
To block access from an unauthorized computer for TCP/IP communication, restrict the range of IP addresses allowed to access the machine. Also, specify the unused protocols to reduce the risk of intrusion.
Encrypting the network communication
Reduce the risk of information leaks by encrypting communication between this machine and the computers or external devices. For encryption, installation of the Device Certificate is required.
