

  |  | ||
This can be specified by the administrator.
To protect the communication path and establish encrypted communication, create and install the device certificate.
There are two ways of installing a device certificate: create and install a self-signed certificate using the machine, or request a certificate from a certificate authority and install it.
SSL (Secure Sockets Layer)
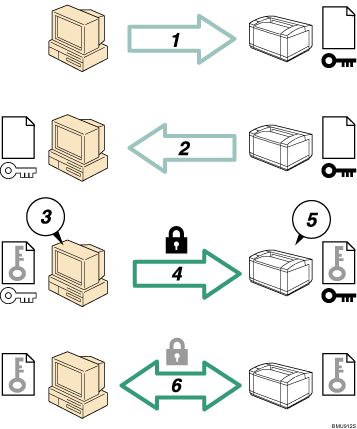
To access the machine from a user's computer, request the SSL device certificate and public key.
The device certificate and public key are sent from the machine to the user's computer.
Create a shared key from the user's computer, and then encrypt it using the public key.
The encrypted shared key is sent to the machine.
The encrypted shared key is decrypted in the machine using the private key.
Transmit the encrypted data using the shared key, and the data is then decrypted at the machine to attain secure transmission.
Configuration flow (self-signed certificate)
Creating and installing the device certificate
Install the device certificate using Web Image Monitor.
Enabling SSL
Enable the "SSL/TLS" setting using Web Image Monitor.
Configuration flow (certificate issued by a certificate authority)
Creating the device certificate
Create the device certificate using Web Image Monitor.
The application procedure after creating the certificate depends on the certificate authority. Follow the procedure specified by the certificate authority.
Installing the device certificate
Install the device certificate using Web Image Monitor.
Enabling SSL
Enable the "SSL/TLS" setting using Web Image Monitor.
![]()
To confirm whether SSL configuration is enabled, enter "https://(the machine's IP address or host name)/" in your Web browser's address bar to access this machine. If the "The page cannot be displayed" message appears, check the configuration because the current SSL configuration is invalid.