Configuring the machine to use SSL/TLS enables encrypted communication. Doing so helps prevent data from being intercepted, cracked, or tampered with during transmission.
Flow of SSL/TLS encrypted communications
To access the machine from a user's computer, request the SSL/TLS device certificate and public key.
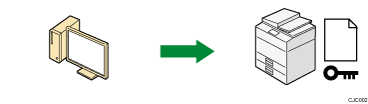
The device certificate and public key are sent from the machine to the user's computer.
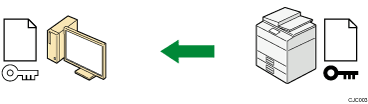
The shared key created with the computer is encrypted using the public key, sent to the machine, and then decrypted using the private key in the machine.
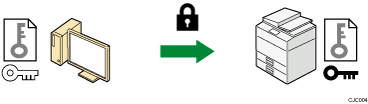
The shared key is used for data encryption and decryption, thus achieving secure transmission.
Configuration flow when using a self-signed certificate
Creating and installing the device certificate:
Create and install a device certificate from the control panel or Web Image Monitor.
Enabling SSL/TLS:
Enable the SSL/TLS setting using Web Image Monitor.
Configuration flow when using an authority issued certificate
Creating a device certificate and applying to the authority:
After creating a device certificate on Web Image Monitor, apply to the certificate authority.
The application procedure after creating the certificate depends on the certificate authority. Follow the procedure specified by the certificate authority.
Installing the device certificate:
Install the device certificate using Web Image Monitor.
Enabling SSL/TLS:
Enable the SSL/TLS setting using Web Image Monitor.
![]()
To check whether SSL/TLS configuration is enabled, enter "https://(the machine's IP address or host name)/" in your Web browser's address bar to access this machine. If the "The page cannot be displayed" message appears, check the configuration because the current SSL/TLS configuration is invalid.
If you enable SSL/TLS for IPP (printer functions), sent data is encrypted, preventing it from being intercepted, analyzed, or tampered with.