Configuring the IPsec Policy
Click the [IPsec Policy List] tab on the IP security settings page to display the list of registered IPsec policies.
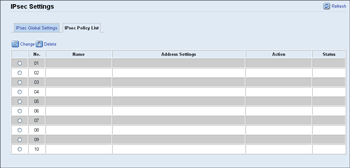
Item |
Description |
|---|---|
No. |
IPsec policy number. |
Name |
Displays the name of the IPsec policy. |
Address Settings |
Displays the IP address filter of the IPsec policy as below: Remote address/Prefix length |
Action |
Displays the action of the IPsec policy as “Allow”, “Drop”, or “Require Security”. |
Status |
Displays the status of the IPsec policy as “Active” or “Inactive”. |
To configure IPsec policies, select the desired IPsec policy, and then click [Change] to open the “IPsec Policy Settings” page. The following settings can be made on the “IPsec Policy Settings” page.
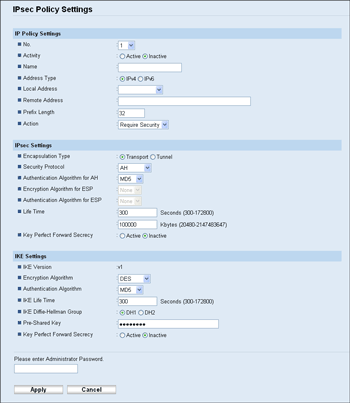
Item |
Description |
|---|---|
No. |
Specify a number between 1 and 10 for the IPsec policy. The number you specify will determine the position of the policy in the IPsec Policy List. Policy searching is performed according to the order of the list. If the number you specify is already assigned to another policy, the policy you are configuring will take the number of the earlier policy, and the earlier policy and any subsequent policies will be renumbered accordingly. |
Activity |
Select whether to enable or disable the policy. |
Name |
Enter the name of the policy. Can contain up to 16 characters. |
Address Type |
Select IPv4 or IPv6 as the type of IP address to be used in IPsec communication. |
Local Address |
Displays the IP address of this printer. |
Remote Address |
Enter the IPv4 or IPv6 address of the device with which to communicate. Can contain up to 39 characters. |
Prefix Length |
Enter the prefix length of the Remote Address, using a value between 1 and 128. If this setting is left blank, "32" (IPv4) or "128" (IPv6) will be automatically selected. |
Action |
Specify how the IP packets are processed from the following:
If you have selected [Require Security], you must configure [IPsec Settings] and [IKE Settings]. |
Item |
Description |
|---|---|
Encapsulation Type |
Specify the encapsulation type from the following:
|
Security Protocol |
Select the security protocol from the following:
|
Authentication Algorithm for AH |
Specify the authentication algorithm to be applied when [AH] or [ESP&AH] is selected for [Security Protocol] from the following: [MD5], [SHA1] |
Encryption Algorithm for ESP |
Specify the encryption algorithm to be applied when [ESP] or [ESP&AH] is selected for [Security Protocol] from the following: [None], [DES], [3DES], [AES-128], [AES-192], [AES-256] |
Authentication Algorithm for ESP |
Specify the authentication algorithm to be applied when [ESP] is selected for [Security Protocol] from the following: [MD5], [SHA1] |
Life Time |
Specify the life time of the IPsec SA (Security Association) as a time period or data volume. The SA will expire when the time period you specify elapses or the volume of data you specify reaches the volume carried. If you specify both a time period and a data volume, the SA will expire as soon as either is reached, and a new SA will then be obtained by negotiation. To specify the life time of the SA as a time period, enter a number of seconds. To specify the life time of the SA as a data volume, enter a number of KBs. |
Key Perfect Forward Secrecy |
Select whether to enable or disable PFS (Perfect Forward Secrecy). |
Item |
Description |
|---|---|
IKE Version |
Displays the IKE version. |
Encryption Algorithm |
Specify the encryption algorithm from the following: [DES], [3DES], [AES-128], [AES-192], [AES-256] |
Authentication Algorithm |
Specify the authentication algorithm from the following: [MD5], [SHA1] |
IKE Life Time |
Specify the life time of the ISAKMP SA as a time period. Enter a number of seconds. |
IKE Diffie-Hellman Group |
Select the IKE Diffie-Hellman Group to be used in the generation of the IKE encryption key from the following: [DH1], [DH2] |
Pre-Shared Key |
Specify the PSK (Pre-Shared Key) to be used for authentication of a communicating device. Can contain up to 32 characters. |
Key Perfect Forward Secrecy |
Select whether to enable or disable PFS (Perfect Forward Secrecy). |
![]()
For details about IPsec, see Transmission Using IPsec
 .
.

